Overview
The Gordian PSIRT team is responsible for maintaining security standards for Gordian products by assessing and minimizing customer risk associated with security vulnerabilities by providing timely information, guidance and remediation for vulnerabilities in our products. The Gordian global PSIRT team manages the receipt, investigation, remediation and public reporting or information about security vulnerabilities related to Gordian products. Key responsibilities of the Gordian PSIRT team are to intake, triage, respond to and disclose externally identified vulnerabilities in Gordian products.
Definitions
CVE – Common Vulnerabilities and Exposures – A standardized system for identifying and naming security vulnerabilities in software and hardware products. Each CVE entry is assigned a unique identifier that allows security professionals, vendors and users to reference and track specific vulnerabilities. CVE entries provide detailed information about the vulnerability, including its description, impact, affected products and recommended mitigation measures. This standardized naming scheme helps in the consistent identification, tracking and sharing of vulnerability information across the cybersecurity community.
CVSS – Common Vulnerability Scoring System – A standardized framework for assessing and quantifying the severity and impact of security vulnerabilities. It provides a methodical approach to evaluating vulnerabilities based on various metrics, enabling consistent and objective vulnerability prioritization. The CVSS framework assigns numeric scores to vulnerabilities, considering factors such as exploitability, impact on confidentiality, integrity and availability, as well as any additional environmental factors.
CWE – Common Weakness Enumeration – A community-driven list of common software weaknesses and vulnerabilities. CWE provides a comprehensive taxonomy of software weaknesses, classifying them into different categories and describing their characteristics, consequences and potential mitigations. Each weakness in the CWE list is assigned a unique identifier, allowing software developers, security analysts and researchers to refer to specific weaknesses consistently. CWE is widely used as a reference for identifying and addressing vulnerabilities during software development, vulnerability assessments and secure coding practices.
Incident – Any unexpected event or occurrence that disrupts or threatens the normal functioning, security or operations of a system or organization. Incidents can include security breaches, unauthorized access attempts, system failures, data breaches or any other event that requires investigation, response and mitigation.
OSINT – Open Source Intelligence – refers to the collection, analysis and use of publicly available information from open sources, including the internet, social media, public records and other publicly accessible resources. OSINT is used for various purposes, including gathering intelligence, conducting investigations, assessing risks and understanding the security posture of organizations or individuals. It plays a crucial role in cybersecurity by providing valuable insights for threat intelligence, vulnerability assessment and incident response.
PSIRT – Product Security Incident Response Team – A dedicated group within an organization that focuses on addressing security vulnerabilities and incidents related to the organization’s products or services. The PSIRT coordinates vulnerability disclosures, analyzes risks, provides guidance on mitigations, facilitates communication between stakeholders, and detects, analyzes and responds to security incidents.
Risk – Refers to the likelihood and potential impact of a threat exploiting a vulnerability and causing damage to assets, systems or data.
Vulnerability – A weakness or flaw in a system, application or network that can be exploited by an attacker to compromise its confidentiality, integrity or availability. Vulnerabilities can exist in software, hardware, configurations or human practices, and they pose potential security risks.
Vulnerability Handling – Refers to the process of identifying, assessing and managing vulnerabilities in a systematic manner. This involves activities such as vulnerability scanning, vulnerability assessment, risk analysis, prioritization and remediation. The goal of vulnerability handling is to minimize the potential impact of vulnerabilities by effectively addressing them through appropriate mitigation measures, such as patches, configuration changes or other security controls.
Reporting
Gordian welcomes reports of potential product vulnerabilities from independent researchers, industry organizations, vendors, customers and others concerned with product security.
To report a potential vulnerability, please use the Report a Potential Vulnerability form below.
Escalation Procedures
Gordian offers a clear and easily accessible reporting channel via a secure contact form on the Report a Vulnerability page. Each form submission generates a ticket which is reviewed by a member of our PSIRT team.
Responsible disclosure reports will receive an automatic response indicating that we have received their submission. A member of our PSIRT team will reach out to the reporter with the vulnerability verification results.
Time to remediation is determined by the vulnerabilities’ priority level; please see Incident Classification below. Public disclosure of a Gordian vulnerability may be disclosed within the product release notes.
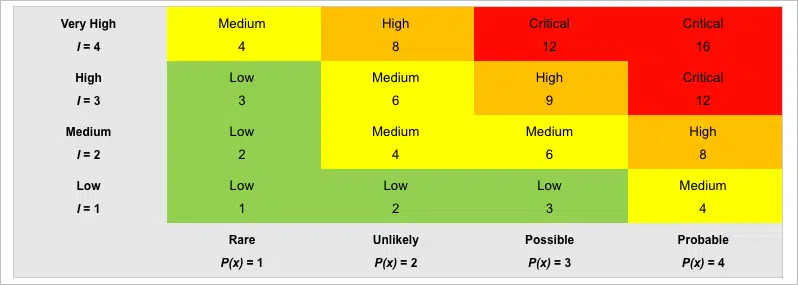
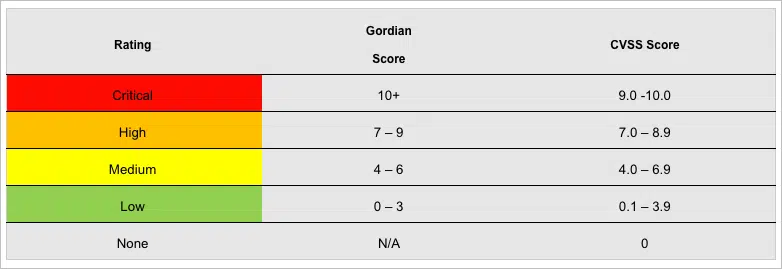
Vulnerability Classification
Priority levels can be further explained by the tables below.
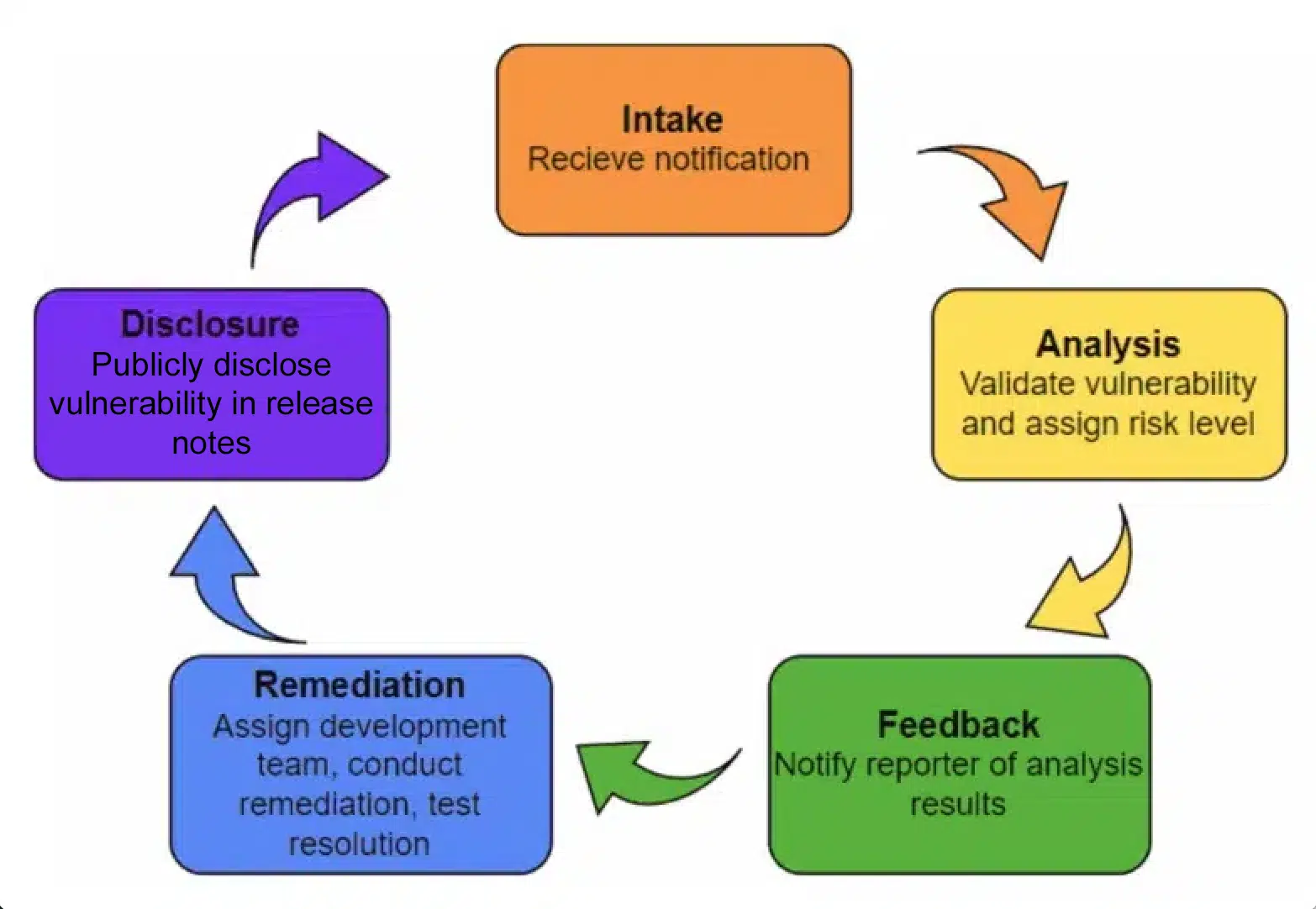
3.8 PSIRT Vulnerability Management Process
The vulnerability management process is a systematic approach to identifying, assessing, prioritizing and addressing vulnerabilities within Gordian applications. It involves a series of activities aimed at reducing the risk posed by vulnerabilities and ensuring the overall security of our organization’s offered products.
Vulnerability triage steps are as follows:
- Intake: Receive vulnerability report and acknowledge receipt.
- Analysis: Identify vulnerability from internal source and verify the report. Verify the vulnerability.
- Feedback: Inform reporter of vulnerability verification status.
- Remediation: Develop and deploy remediation.
- Disclosure: Publish advisory within release notes. Engage in post-remediation activities.
Vulnerability Management
Identification Procedure – A PSIRT engineer will review the findings produced by the external reporter. OSINT may be conducted to gather more information about the vulnerability with an attempt to determine CVE and CWE, if not provided by the reporter. The reported vulnerability will be compared to current and past reports and remediations to determine if it is an existing, known vulnerability.
Assessment Procedure – Investigation often involves the PSIRT member or assigned developer attempting to reproduce the environment and behavior reported by the reporter. Static code analysis or other internal investigation techniques may be used to determine the validity of the finding. This can be a preliminary investigation, focused primarily on the need for further effort by Gordian. The investigation determines whether the report constitutes a vulnerability. A PSIRT member will communicate with the reporter during the investigation, and the vendor notifies the reporter of the results at the end of the investigation. This phase is often called “triage.” If the vulnerability is verified, prioritization will ensue.
Prioritization Procedure – Prioritization is dependent on severity level. Severity level is determined by the relative likelihood and the level of impact of the vulnerability in question being exploited. Associated CVEs and CWEs may aid in determining the vulnerability’s severity level.
The aspired response time for initial contact from a PSIRT member to a vulnerability reporter is 72 hours. Follow-up communications may occur between the time of positive vulnerability validation and vulnerability disclosure within product release notes.
Gordian takes security concerns seriously and prioritizes their prompt evaluation and approach. Response timelines will depend on a number of factors including the severity and impact, specific product or feature affected, the current product development cycle and the technical requirements needed to properly address the concern or issue. Remediation may include any of the following actions:
a. A new product release
b. A Gordian security update
c. Third-party-directed update installation or patch
d. Other procedural approach to mitigate the vulnerability or concern
Gordian is dedicated to the prompt resolution of all potential or actual security vulnerabilities but does not guarantee any specific remediation or resolution for reported concerns.
Coordination with Stakeholders
In addition to the Gordian PSIRT team outlined above, Gordian may employ commercial incident investigation firms if necessary to properly address any given issue.
PSIRT team communication tools include those approved for corporate use for widespread communication within Gordian and for the project and task tracking of engineers. This is how Gordian will disseminate information to appropriate stakeholders.
Report a Potential Vulnerability
To report a vulnerability, please fill out the form below. We aspire to respond to researchers within 72 hours regarding the status of the potential finding. We appreciate your patience and dedication to improving the security of products at Gordian.